You can access the full course here: JR CODERS – MANAGING DATA IN NETWORKED SYSTEMS
Encryption
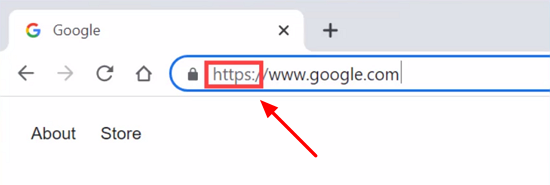
Encryption is used for logging into websites and transferring files over the Internet. You may have noticed that most pages you visit have URLs starting with ‘https‘. This means they are using the Transport Layer Security (TLS) protocol to encrypt the data sent to and from the website:
But how can a client and server communicate through encrypted messages without a third party being able to spy on them and see the contents exchanged?
- It starts with the client establishing a connection with the server by sending over a number of random bytes:

- The server responds with its own random number, along with its public key and SSL certificate to prove they are indeed the host of the domain:

The server public key can only be used to encrypt data.
- The client then generates a secret key which is encrypted using the server’s public key and sends it over to the server:

- The server can decrypt the data using his private key (associated with the public key used by the client) to retrieve the secret key, so both client and server have the secret key too at this point:

- Using the secret key and random bytes exchanged at the beginning, they can generate a session key (which should be the exact same on both sides):
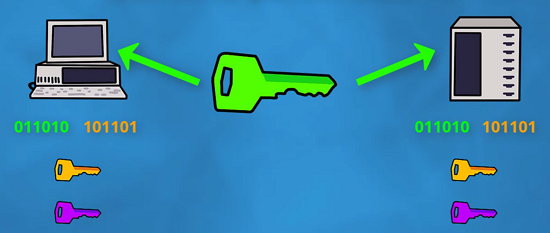
- Now they can both encrypt and decrypt using this session key as it’s only known by them and nobody else:

Anyone looking at it from the outside wouldn’t be able to get the secret key and, hence, the session key is also secure.
Transcript
When logging into a website or transferring files over the internet, encryption is used to obscure your data.
You may notice that most websites you visit, the URL, it doesn’t start with the typical HTTP, but rather HTTPS. This means that the transport layer security protocol is being used to encrypt the data sent to and from the website.
So how can a client and server communicate with each other cryptically without a third party being able to spy in on them and see what they’re sending each other?
Well, it starts with the client establishing a connection with the server, sending over a number of random bytes.
In response, the server sends over its own number of random bytes, as well as an SSL certificate to verify that they are, indeed, the host of the domain.
Along with this message is also the server’s public key. Anyone can see it as it can only be used to encrypt data, not decrypt it. The client then generates a secret key, which is encrypted using the server’s public key, and sent over.
Now, since the client encrypted that data using the server’s public key, the server has its own private key, which nobody else knows about, that it can use in order to decrypt that message.
At this point, both the client and the server have the secret key, as well as the random bytes that they sent each other. Using these three things, they can both generate a session key, which should be the exact same.
Now they can both encrypt and decrypt messages using this key, as it’s only known to the both of them. Anyone looking in from the outside will only have two pieces of this three-piece puzzle, okay?
That secret key that the client created and sent over, nobody else can really get that, apart from the client and the server, so they can use that to generate the session key.
Interested in continuing? Check out our all-access plan which includes 250+ courses, guided curriculums, new courses monthly, access to expert course mentors, and more!